Rodrigo Bazo, Leonardo Boldrini, Cristian Hesselman, Paola Grosso
In January 15th, the kickoff meeting for the User-driven Path verification and control for Inter-domain Networks (UPIN) project was held with all projects partners. At the kickoff, the core ideas of the project and its details were presented and discussed which are condensed in this first blog post as well. The UPIN project is a partnership between the University of Twente and the University of Amsterdam with the following industry partners: NLnet Labs, SIDN Labs and SURF. The project is funded by the Dutch Research Council (NWO).
Current Internet vs. Future Applications
Nowadays, smart-cities solutions are moving from the domain of ideas to reality. Self-driving vehicles, delivery and healthcare drones, autonomous supply chains… these are only some examples of futuristic technologies that are just around the corner and should see market-wide adoption in the coming years. These new technologies have a direct and effective impact on the real world, since their components often interact with physical space and therefore introduce safety risks, thus being directly responsible for human lives (e.g. doctor performing a remote surgery; autonomous vehicles). The effects of unexpected network events in these cases could result in losses that range from measurable losses such as cars colliding or unmeasurable losses such as people’s lives. The root cause of these issues are due to inherent limitations on current Internet infrastructure [2,3] (e.g. lack of transparency for users; lack of validation over data paths). Efforts towards solving these problems exist and range from new security additions to existing mechanisms and protocols such as RPKI [8] and BGPsec [7] to proposals of a completely new Internet design, such as SCION [6]. Furthermore, the current Internet architecture is completely “Black Boxed”, which is also a threat to user’s privacy due to it’s lack of transparency, accountability and controllability [4]. By making the Internet more controllable and transparent, larger user trust can be achieved since the paths that data follows can be validated.
UPIN Project: Motivations and Specifics
How do we make the Internet more transparent and provide Internet users with more control over and verifiability of network paths in a scalable way? To what degree can the current Internet architecture accommodate these functions and which other emerging inter-network architectures might potentially be more suitable? These are some of the question that motivate the UPIN project.
In UPIN we aim at giving some control to the user on how their data will travel through the network (e.g. routing data only through BGPsec-enabled routes). The main mechanisms that we intend to use in order to achieve that are: Path Control and Path Verification, namely, mechanisms for enforcing the packets to follow determined paths and ability to verify if packets followed paths matching user criteria. This way, users can avoid their data to follow paths that they consider untrusted (e.g. paths on ISPs which don’t traverse routers from specific manufacturers).
Architecture
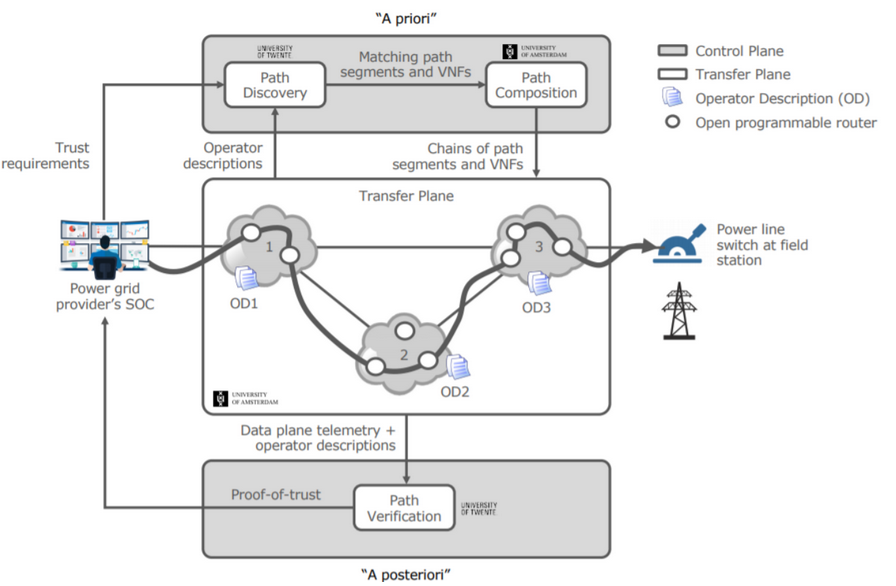
In Figure 1, the latest version of the UPINs architecture is depicted, showing the user’s data being routed through networks according to the source’s specific trust requirements and using attestation of the routers in the network. The architecture is composed of the following main components:
-Path Discovery: Gathers information about possible paths that meet the user’s trust requirements based on network operator and router properties
-Path Composition: Composes paths based on the combination of the user trust requirements and path discovery data
-Path Verification: Verifies the path followed by packets and feedbacks a proof-of-path back to the user.
Testbed
We intend to tackle the problem by using available tools with potential to assess such limitations, to cite some: Software-defined Networks (SDN), Network Virtual Functions (NVF) and Segment Routing (SR).
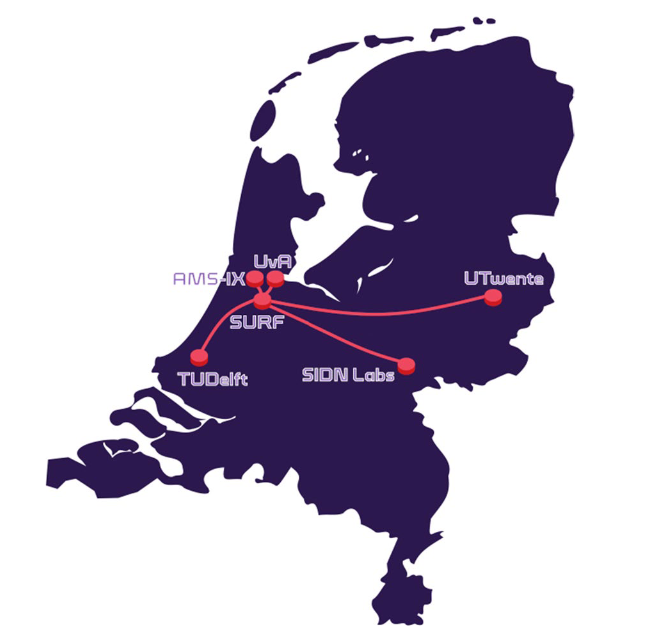
The UPIN prototype will be deployed and experimented on the 2STiC testbed [5, 2], a national multi-domain setup of P4-programmable routers interconnected in a star-shaped optical network.
Figure 2 depicts the testbed.
This research received funding from the Dutch Research Council (NWO).
References
[1] Stability 2STiC: Security and Transparency in inter-network Communica-tion. https://2stic.nl/, 2021.
[2] Cristian Hesselman, Paola Grosso, Ralph Holz, Fernando Kuipers, Janet HuiXue, Mattijs Jonker, Joeri de Ruiter, Anna Sperotto, Roland van Rijswijk-Deij, Giovane CM Moura, Abhishta, Luca Allodi, Chrysa Papagianni,Bart Nieuwenhuis, Aiko Pras, and Cees de Laat.A responsible in-ternet:increasing trust in the foundation of digital societies (part 1of 2) – https://www.sidnlabs.nl/en/news-and-blogs/a-responsible-internet-increasing-trust-in-the-foundation-of-digital-societies. Accessed in February2021.
[3] Cristian Hesselman, Paola Grosso, Ralph Holz, Fernando Kuipers, Janet HuiXue, Mattijs Jonker, Joeri de Ruiter, Anna Sperotto, Roland van Rijswijk-Deij, Giovane CM Moura, Abhishta, Luca Allodi, Chrysa Papagianni, BartNieuwenhuis, Aiko Pras, and Cees de Laat.A responsible internet: the chal-lenges ahead (part 2 of 2) – https://www.sidnlabs.nl/en/news-and-blogs/a-responsible-internet-the-challenges-ahead. Accessed in February 2021.
[4] Cristian Hesselman, Paola Grosso, Ralph Holz, Fernando Kuipers, Janet HuiXue, Mattijs Jonker, Joeri de Ruiter, Anna Sperotto, Roland van Rijswijk-Deij, Giovane CM Moura, et al. A responsible internet to increase trust inthe digital world.Journal of Network and Systems Management, 28(4):882–922, 2020.
[5] L. Hendriks J. Hill R. van der Pol V. Reijs J. de Ruiter C. SchutijserP. Grosso, C. Hesselman and S. Konstantaras. A national programmable in-frastructure to experiment with next-generation networks.2021 IFIP/IEEEInternational Symposium on Integrated Network Management (IM 2021),2021.
[6] Adrian Perrig, Pawel Szalachowski, Raphael M Reischuk, and LaurentChuat.SCION: a secure Internet architecture. Springer, 2017.
[7] Noction Network Intelligence BGP security: an overview of the RPKI frame-work. https://www.noction.com/blog/rpki-overview, 2021.
[8] Noction Network Intelligence BGP security: the BGPsec protocol.https://www.noction.com/blog/bgpsec-protocol, 2021.
